It’s a Monday morning. You are checking your email, and amid the usual flow of messages, one stands out: “Notification from SARS.”The tone is official. The logo is perfectly placed. The sender’s address looks authentic, and even the government domain appears genuine. Out of habit, you click to read more. After all, it’s the tax authority; you cannot ignore that.
But beneath the polished façade lies a trap, a phishing email so carefully designed that even seasoned executives can fall for it. The link inside, web.val.run, looks harmless but leads to a fake login page, a digital decoy built to harvest your credentials or quietly install malware on your device.
This is not a random attack but a carefully orchestrated con.
Welcome to the age of social engineering.
Modern hackers do not always “break in.” Instead, they invite you to open the door yourself. They study human behavior, mimic trusted institutions, and wait for the perfect moment when you are tired, rushed, or distracted.
In just one careless click, your inbox, bank account, or corporate network could become theirs. Even the most secure devices are not exempt. Many believe that using a Mac or a reputable antivirus guarantees safety.
Today’s phishing kits target browsers, not operating systems. Once you enter your password or approve a fake access request, you have bypassed every firewall, every antivirus, and every system safeguard because you willingly handed them the keys.
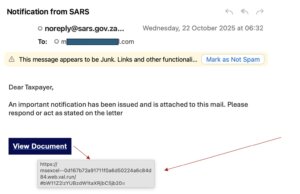
How to stay safe when the ‘government’ emails you
Cybercriminals thrive on trust. They exploit it through fear, urgency, and authority. Here’s how to stay one step ahead:
- Don’t click suspicious links.
If you receive a tax-related or government email, go directly to the official website (for example, www.sars.gov.za) instead of clicking the embedded link. - Verify the full domain.
Look beyond the display name. Cybercriminals use deceptive domains like .run, .info, or .web to trick unsuspecting users. - Hover before you click.
Move your cursor over any link to reveal its true destination. If it looks odd or doesn’t match the official site, it’s a red flag. - Report, do not engage.
Mark such emails as spam or phishing, report them to your IT team or service provider, and delete them. Never mark a suspicious email as “Not Spam.” - Enable two-factor authentication (2FA).
It’s your safety net, the last line of defense if you accidentally share credentials. Even if hackers get your password, they won’t get past your second factor.
Cybersecurity is about instincts, not just infrastructure.
Firewalls, antivirus software, and secure systems matter, but so does awareness. The most advanced system can’t protect you from your own click.
In an era of perfect impersonation, where even a government email can be forged, your greatest defense is critical thinking.
Cybersecurity isn’t about having stronger walls. It’s about cultivating sharper instincts. Trust must now be verified, not assumed.
I remain, Mr. Strategy







