I have learned that intelligence does not protect organisations from failure. In many cases, it accelerates it. In 1999, engineers finished the Millennium Bridge in London. On paper, it was flawless. Elegant design. Brilliant minds. World-class modelling. On opening day, the bridge began to sway, not because of poor engineering, but because people adjusted their walking unconsciously in response to movement. Each correction amplified the wobble. Intelligence created feedback loops no one anticipated. The bridge did not fail because it was weak, but because it was smart in the wrong way. That is how smart teams still make dumb decisions.…
NGO fraud red flags and why cybersecurity and fraud risk assessment are now urgent in a resource-constrained context
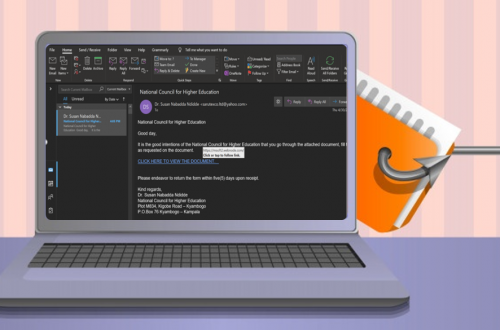
The incident began in early 2024 within the operational accounts of an international non-governmental organisation headquartered in Kampala. Funds earmarked for water, sanitation, and health projects were diverted systematically over several months. Donor reports showed deliverables vastly out of alignment with cash outflows. At first glance, auditors thought this was a routine bookkeeping error, but a deeper trace revealed an emerging pattern. Payments to known vendors were routinely misstated, descriptions altered, and receipts fabricated. The red flags did not emerge from one misplaced figure, but from a cascade of small anomalies that, when stitched together, painted a coherent picture of…
Board structure for effective committee intersection and oversight tool
I have observed that many boards are inefficient because committees operate perfectly in isolation. After years of evaluating boards across financial institutions, manufacturing firms, and state entities, one pattern repeats, Audit reviews controls, Risk reviews exposure, and Credit review portfolios. Nomination and Governance reviews succession. Each reports upward. Few connect sideways. On paper, everything looks covered. Under stress, gaps appear. The Board Committee Intersection & Oversight Alignment Map is designed to expose those gaps before a crisis occurs. It forces clarity on ownership, joint accountability, escalation triggers, incentive alignment, and capability gaps. It makes visible where oversight overlaps, where it…
Directors come unprepared yet speak the most
Boards do not fail in crisis; they fail in meetings. After over twenty-five years sitting in boardrooms as advisor, evaluator, director, secretary and sometimes quiet confidant, one pattern remains constant. The loudest voices are often the least prepared. And the cost is rarely visible immediately. It shows up later in missed risks, defensive CEOs, passive chairs, frustrated company secretaries, and strategy that drifts. Usually, this is not a character flaw. It is a governance design issue. Preparation, airtime discipline, and psychological courage are not personality traits. They are board setup choices. When they are weak, ego fills the gap, and…
Appreciation Note to IDRC’s ED, Prof. Moses Kamya
Some leaders do not need to introduce themselves. Their work does it for them; quietly, consistently, and unmistakably.Prof. Moses Kamya, Executive Director of the Infectious Diseases Research Collaboration (IDRC), is such a leader. A man whose global exposure, academic excellence, and unmatched professional stature could easily have created distance, yet he chooses a different path. He listens. He empowers. He creates room for young professionals and local consultants to shine. That is the mark of true leadership, confidence without arrogance, authority without intimidation, and brilliance without noise.In 2019, I had the privilege of working with IDRC on Strategy and Enterprise-Wide…
Who I am, and why I am uncomfortable in strategy retreats
I learned long ago that strategy retreats are the corporate equivalent of a well-lit comedy room. Everyone enters with optimism, speaks with measured confidence, and leaves with a perfectly framed set of commitments that die within weeks. I do not get uncomfortable because retreats are bad. I get uncomfortable because retreats are dishonest, not maliciously dishonest, but structurally dishonest. They reward posture over truth, comfort over clarity, and performance over leadership. The first time I realised this, I was facilitating a retreat for a large public-sector organisation. The room was beautiful. The banners were crisp. The participants were seniors. But…