Mustapha B Mugisa, aka Mr Strategy was honoured to speak at the 2024 East African Banking Schools Conference jointly organized by the Banking Institute’s of Uganda, Kenya and Tanzania. Due to demand, we share excerts from his speech, verbatim.
“How many of you have connected to the Internet this morning? Now, how many of you used WiFi to connect? And how many of you used the hotel WiFi?”
“Many of you, I see. Do you know that when you connect via someone else’s WiFi, especially public networks like in hotels, cafes, or airports, you potentially expose yourself to significant risks? Let me explain how.”
“When you use public WiFi, you are entering a digital space that is much less secure than your private home network. It’s like having a conversation in a crowded room—others can overhear you unless you take steps to protect your privacy”
Here’s how hackers exploit public WiFi to access your data
- Man-in-the-Middle Attacks. Here, asyou send data from your laptop or phone to the WiFi router, hackers can intercept this data. Imagine sending a sealed letter through several couriers, one of whom opens it, reads it, maybe even changes the content, then reseals it and sends it on without you knowing.
- Evil Twin Attacks. This is a devious one, as its name. Hackers set up a WiFi network that looks almost identical to the one you intend to use. Once you connect to this ‘evil twin’, they can monitor everything you do online. For example, if your hotel WiFi is named “Sheraton.” The hackers may set theirs and name it “Sheraton Hotel”, thereby fooling you into thinking it is another one set up by the hotel. Once you connect on their evil network, they log into your computer.
- Packet Sniffing. With generative AI making malware is easy.Hackers can easily capture and analyze the data passing over the network. This might include emails, passwords, messages, and even sensitive financial information. For this reason, you are always advised to never connect to sensitive services via public WiFi.
- Planting Malware. Through unsecured WiFi, hackers can easily plant malware on your device, which can monitor your activities, steal data, and even take over your device without your knowledge.
“If you have a mobile device with you, raise it up.” Turn to your neighbour and ask: How many times have you used your device to lie? Where you are using your device to lie or others are lying through your device, in today’s technological era, any thing is possible.
Welcome to the discussion on the future we are building.
A few years ago, a renowned tech company faced a massive data breach affecting over 147 millions. Instead of immediate disclosure, they chose silence, prioritizing stock prices over people’s privacy. This incident poses a critical question to all of us in this room: What is the role of ethics in technology?”
In the next 15 minutes, we will explore technological era ethical dilemas and how to manage the risks.
Slide 2: The Power of Technology
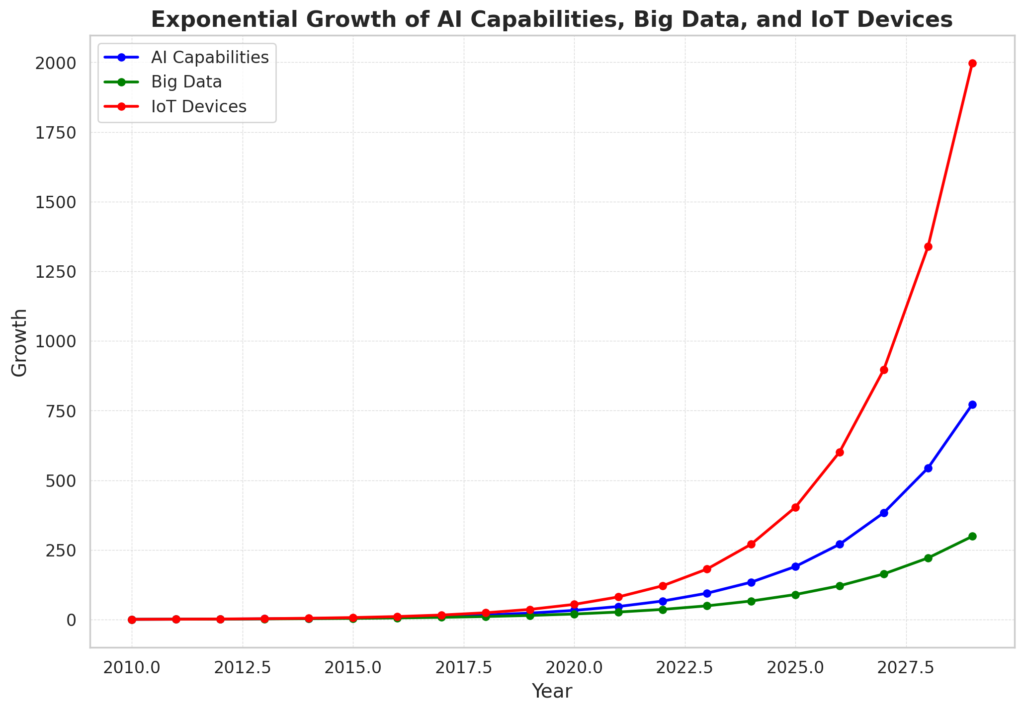
In the graph, you can see the exponential growth in AI capabilities, bi data, and IoT devices.
As technology’s footprint expands, so does its ethical footprint. Every new tool and dataset can significantly impact society in ways both intended and unintended.”
One of the reasons we conduct mandatory monthly ethical training to staff in our digital forensics lab is the thin line between personal data on the suspect machine and business data. You have these powerful tools that will bring all data. One traumatizing case is where a suspect had backups of his home cctv camera footable on his phone. What do you think most people would do finding footage in compromising situations? Sell it? Not open all? Delete?
“Take a moment to think about a recent technological advancement that impressed you. Now, consider the potential ethical implications it might carry. Share your thoughts with the person next to you.”
Ethics in AI Development
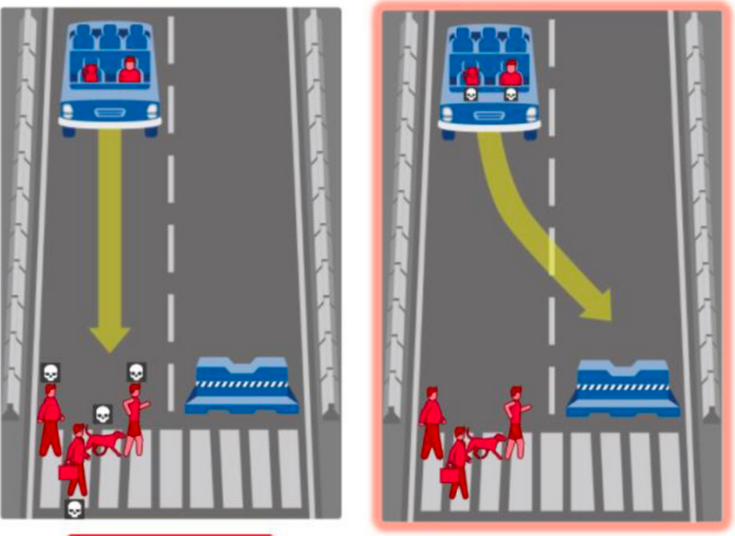
The photo above shows the ethical challenges in developing and deploying Tesla’s Autopilot or any self driving car showing an ethcial a dilemma scenario where harm is unavoidable.
“How do we program machines to make moral decisions? Should an autonomous vehicle prioritize the safety of its passengers or pedestrians?”
“Raise your hand if you believe the primary responsibility of an autonomous vehicle is to protect its passengers first. Now, raise your hand if you think it should prioritize pedestrians. This diversity in opinions showcases the complexity of ethical decision-making in AI.”
Another critical point is the potential for AI in lending decisions condemning an entire generation of people; where they are profiled as bad borrowers in which no one qualifies for the loan.
In the long term, such population analyzed with poor repayment history may fail to get credit facilities they need to improve their financial condition.
Integrity in Data Privacy
Analysis of the Facebook and Cambridge Analytica scandal.
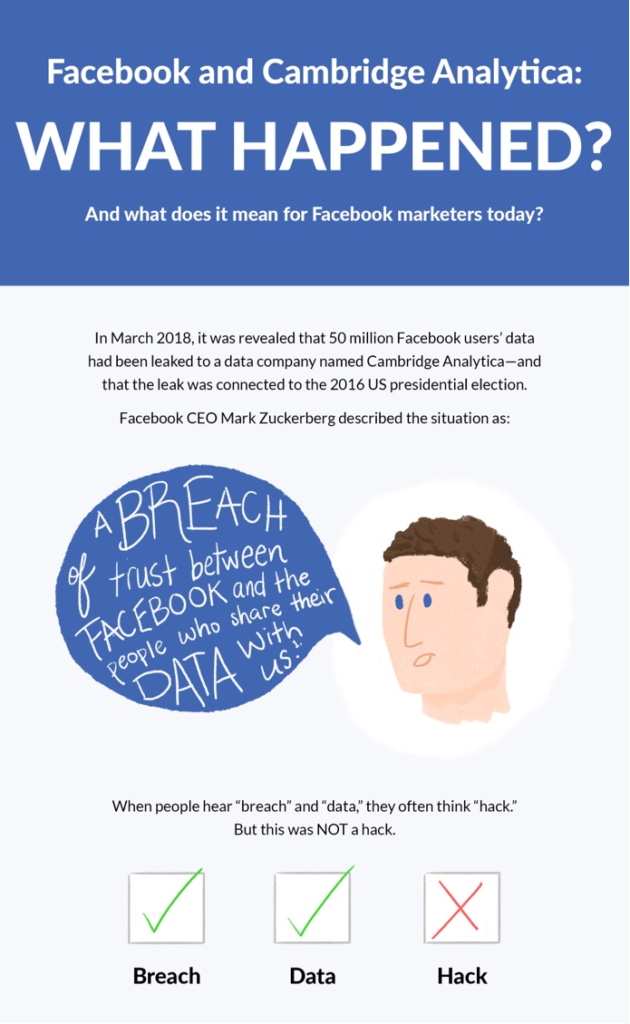
Source: Online
“The Facebook data breach scandal highlights the critical importance of data integrity. It’s not just about protecting data from hackers but also about how data is ethically gathered, used, and shared.”
“Imagine you are the CEO of a company that has just discovered a major data breach. What are the first three steps you would take to address the issue? Write them down and discuss with your neighbor.”
Professionalism and Tech Companies

The controversy around Google’s Project Maven and the ethical stance of employees.Remember the Google employee protests and public reactions? That was their ethics at play .
They felt that is not what they joined Google to do, as the project had potential to cause harm on a grand scale.
“Professionalism in tech isn’t just technical competence; it includes ethical congruence between a company’s actions and its stated values, as well as the moral courage of its employees to hold it accountable.”
“Think about a time when you or your organization faced an ethical dilemma. How did professionalism guide your response? If you’re comfortable, share your story with the group.”
Practical Steps Towards Ethical Tech
- Checklist Graphic:Detailed guide for implementing ethical practices in tech companies.
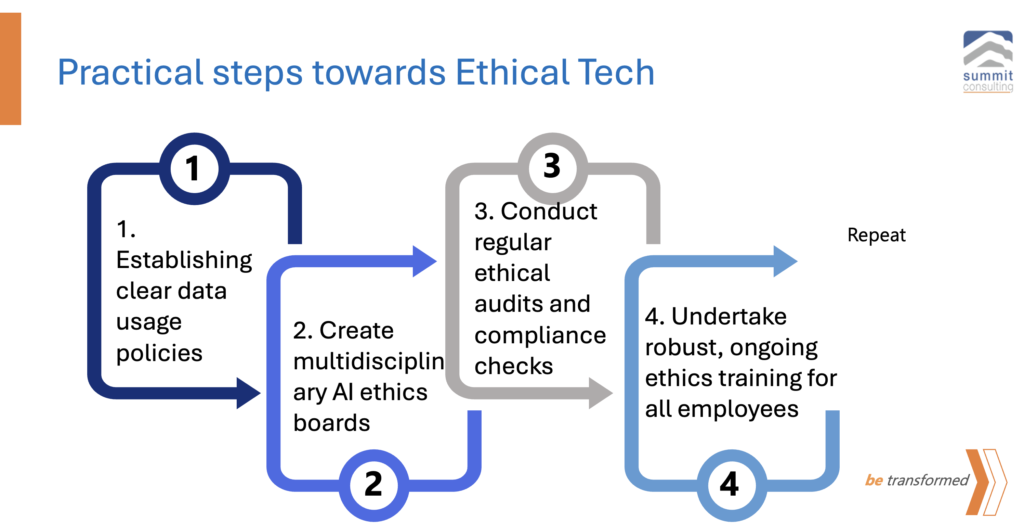
Establish clear, transparent data usage policies. Organizations should have well-documented policies that define how data is collected, stored, used, and shared. These policies should be accessible and understandable to all stakeholders. For example, a healthcare company clearly outlines in its data usage policy that patient data will only be used for treatment and research purposes with explicit consent, and not for commercial advertising. The data cannot be used for any other thing that is not explicity defined in the policy.
Create multidisciplinary AI ethics boards. An AI ethics board should include members from diverse professional backgrounds such as ethics, law, technology, and public policy to provide well-rounded guidance on ethical AI usage. For example, a tech firm forms an AI ethics board consisting of a philosopher, a data scientist, a legal expert, and a civil rights advocate to evaluate and guide the ethical implications of AI projects.
Conduct regular ethical audits and compliance checks. Regular audits are necessary to ensure that AI practices adhere to ethical standards and regulatory requirements, identifying any deviations and implementing corrective actions. Consider an example of e-commerce company that performs bi-annual audits to review their AI algorithms that recommend products to users, ensuring they don’t inadvertently perpetuate bias or violate privacy norms. You want your AI to not inadvertently exclude a certain section of the population from accessing financing.
Initiate robust, ongoing ethics training for all tech employees. Continuous training programs should be in place to keep all tech-related employees aware of ethical practices and updates in regulations pertaining to AI and data usage. Take an example of a software company that implements a mandatory quarterly training session for all its developers and engineers focusing on new developments in AI ethics, such as fairness in machine learning models or new data protection laws.
Implementing these steps ensures that technology companies not only comply with legal standards but also uphold ethical principles.”
Commit to one practical step you will take to enhance ethical practices in your organization. Write it down and share it with the person next to you. Accountability starts here.
Engaging With Stakeholders
“Ethical technology development requires a collective voices, especially those that challenge the status quo. This leads to more resilient and adaptable ethical standards.”
Consider the stakeholders in your organization. Who might offer a challenging but necessary perspective on your tech practices? Share one stakeholder with the group.
I invite you to share your questions or perspectives on the ethical challenges we face in technology. Your insights are critical as we navigate these complex issues.
In an era of rapid innovation, ethics, integrity, and professionalism must be the pillars upon which all technological advancements are built
Thank you for having me today.









